Agentforce, the GenAI Agent by Salesforce

In light of recent events, the thought of cybersecurity and vulnerability across enterprises are now becoming forefront in the minds of the leaders of many organizations.
By 2018, oil and gas companies are predicted to spend $1.87 billion on cybersecurity, as manufacturing continues to climb in the ranks of most frequently attacked industry. With the price of crude remaining below $50/bbl, why are oil & gas companies investing time and money in cybersecurity? We believe that, in addition to the financial implications of a security breach, there are critical risks in oil & gas organizations that exist due to growth in convergence between Business Enterprise Applications and Operational Technology Applications (OT) in areas such as Process Safety, Equipment Reliability, Production Uptime, HSSE, Company Reputation, and Oil Market Fraud.
In the oil & gas industry, there are various sectors that describe the different processes through the entire chain of extracting crude oil from the ground to refining it to useable products that are sold through retail stores. The sectors are conveniently termed Upstream, Midstream, and Downstream.
Generally, upstream organizations include the Exploration & Production (E&P) of oil and gas. The exploration of oil and gas includes the prospecting, seismic, and drilling activities that take place prior to developing an oil field. The term “upstream” is often inclusive of the wellhead, well, completion, and reservoir; whereas, downstream of the wellhead is often called production or processing.

Figure 1
Midstream often refers to the transporting, processing, and storing of oil. It is also broadly defined as gas treatment, LNG production and regasification plants, along with oil and gas pipeline systems.
Downstream refers to the manufacturing, refining, petrochemicals, and retailing of oil.
According to Symantec Corporation, the world’s biggest cybersecurity firm, 43% of global mining, oil, and gas companies report a security breach at least once a year. Trend Micro Incorporated also performed a study that concluded that 47% of energy organizations reported attacks, which is the highest amount of reports among all corporate sectors, and according to PwC’s Global State of Information Security Survey of 2016, 42% of Oil & Gas Companies report phishing attacks. These surveys, in addition to the history of attacks in the oil and gas industry, make it very clear that oil & gas is a highly targeted industry.
As seen from the details in the Timeline, and in Figure 2, no sector in the Oil & Gas industry is safe from cyber threats.

Figure 2
As previously mentioned, between 42 and 47 percent of energy companies have claimed being victims of cyberattacks, but here are some ideas that we suggest are the reasons why oil & gas companies are the targets.
Economic
· Preventing resource flows to international markets, as with Saudi Aramco in 2012.
· Hackers could obtain confidential data to get an investing edge.
· Hackers could cause Oil Market Fraud by skewing reporting data used and presented by oil & gas companies.
Political
· Political activists could cause an attack on an oil & gas company that could result in an environmental or safety incident, in order to gain additional political supporters.
· The oil & gas industry makes up the majority of some countries’ economies. Attacks could be detrimental to a countries’ revenue.
Malicious Intent
· Physical damage to equipment, affecting production uptime and potentially injuring workers and communities
· Employees out on strike causing a disruption to operations, as seen in Venezuela in 2002.
Regardless of intent, however, the continuous growing risk of a cyberattack is critical in today’s oil & gas industry, as the lines between a company’s Information Technology system and Operational Technology system continue to blur.
Nowadays you have computers running everything. You can create blackouts or oil spills and hurt a lot of people.
Business Enterprise Applications in Oil & Gas
SAP and Oracle are two of the most common enterprise applications that companies use. Specifically in oil & gas, SAP has more than 246,000 customers worldwide including 86% of Forbes 500 and 85% of Fortune 2000 Oil and Gas, while Oracle solutions are used by 100% of Fortune 100 companies. Both applications are used to support a closed-loop view of an oil and gas enterprise, leveraging a common platform for operations and maintenance, in order to gather, analyze, decide, and execute actions across many different elements that drive performance of assets throughout upstream, midstream, and downstream sectors. Such performance elements include:
· Capital and Spend Effectiveness
· Hydrocarbon Supply Chain
· Integrated Digital Oilfield Operations
· Operational Integrity
· Product Lifecycle and Production Optimization
· Asset Management

Figure 3
SAP in Oil & Gas
SAP solutions are implemented in 90% of oil and gas companies and are connected to some critical processes by the means of SAP xMII and SAP Plant connectivity, as shown later on. These implementations mean that more than 70 million barrels per day of oil that are produced are tied to SAP solutions, so if an attack is successful through means of SAP infiltration, cyber criminals can gain over roughly 75% of total oil production. SAP offerings in oil and gas generally include capital and spend effectiveness, integrated digital oilfield operations, hydrocarbon supply chain, and operational integrity. These offerings are achieved through various SAP applications.
Oracle in Oil & Gas
Like SAP, Oracle offers many solutions to fulfill oil and gas requirements. Specifically, Oracle offerings contribute to Product Lifecycle, Asset Management, and Laboratory Information Management Systems (LIMs) through many different Oracle applications.
Operational Technology (OT) includes industrial automation and control systems such as SCADA, Distributed Control Systems (DCS), Programmable Logic Controllers (PLCs), Open Platform Communication (OPC) Servers, and Field Devices, such as instrumentation or analyzers. OT is used to monitor and control the physical processes across oil & gas sectors by means of acquiring process variable data (such as temperatures, pressures, levels, valve positions, etc.) and using this data to automate processes. This automation is made possible by means of electric, mechanical, hydraulic, of pneumatic actuators and control valves. Operational Technology also allows for the automation of Safety Integrity Systems (SIS), that are OSHA required in order to ensure a process does not operate outside of its Process Safety Management (PSM) operating window.
OT in Upstream
From the extraction (drilling) phase to the metering (or loading) phase of the upstream sector of oil & gas, Operational Technology solutions are seen through many applications. Such applications include:
· Pump control systems
· Blow-out prevention systems
· Flaring and venting
· Wellhead management systems
· Manifold management systems
· Net oil measurement systems
· Heater control systems
· Vibration monitoring systems
· Compressor control systems
· Burner management systems (BMS)
· Desalting management systems
· Emergency shutdown systems
· Tank inventory systems
· Tank gauging systems
· Movement management systems
· Fiscal Metering
OT in Midstream
Likewise, Operational Technology solutions are used throughout the Midstream sector.
· Measurement systems
· Movement automation systems
· Order movement management
· Pipeline management systems
· Peak load gas storage systems
· Tank inventory systems
· Tank temperature management systems
· Tank gauging systems
· Product movement systems
· Emergency shutdown systems
OT in Downstream
In addition to the applications previously mentioned in Upstream and Midstream, the following applications are also applicable to the Downstream sector.
· Blending optimization
· Emission monitoring systems
· Loading and terminal automation
· Gas-pump monitoring systems
In the midst of turbulent times in the oil & gas industry, companies are finding it harder to predict their business plans and have to find ways to increase operational efficiency and reduce costs. Doing so, however, organizations are introducing vulnerabilities in areas such as Process Safety, HSSE, Equipment Reliability, and Production Uptime.
The Rise of IoT and Digital Transformation
A technical solution that companies are installing across the oil and gas value chain is known as the Internet of Things (IoT).
IoT is a practice that involves capturing, analyzing, and acting on data generated by a network of objects and machines. In an essence, IoT is able to connect and analyze constantly changing data to the people that need to make decisions based on the data. In the current industry environment, oil and gas companies are treating data as they treat hydrocarbons; data needs to be generated, communicated, stored, and processed. With the development of IoT strategies, businesses across the oil and gas spectrum are benefiting from the new age Digital Transformation. Examples of benefits include:
Although many companies are realizing benefits by implementing IoT, as systems continue to merge and process data is more readily available, threats of a cyberattack are also increasing because Operational Technology systems are interconnecting with Business Enterprise applications. These ideas are shown in Figure 4, which is an example network map of a typical oil and gas company.
In today’s digital age, information is able to quickly flow from the field into the Operational Technology network, further into the Corporate Network, eventually to the end-user, and vice versa. This must mean the same is true for cyber threats, such as Trojans, malware, ransomwares, viruses, etc. This idea is critical since there would be significant implications if there was a cyberattack on an oil & gas organization.
Perhaps greater connectivity is a double-edged sword.
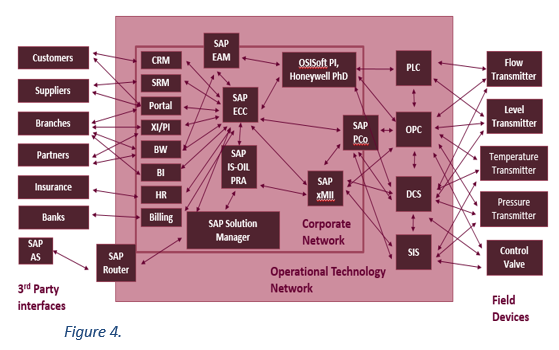
Figure 4
While the below thoughts and scenarios are a collection of ideas that we find important, remember this is not an all-inclusive list of threats that exist to oil & gas companies regarding cybersecurity, nor all-inclusive in risks that Sia Partners acknowledge.
Repeated cyber intrusions into organizations of all types demonstrate the need for improved cybersecurity. Cyber threats continue to grow, and represent one of the most serious operational risks facing modern organizations. The national and economic security of the United States depends on the reliable functioning of the Nation’s critical infrastructure in the face of such threats. Beyond critical infrastructure, the economic vitality of the nation depends on the sustained operation of organization of all types.
As in the UglyGorilla attack in 2012, an attack on U.S. natural gas utilities could allow hackers to access the nation’s 300,000-mile pipeline that is a critical backbone for the nation’s economy. Since the 2012 attack, there has been a significant increase in reliance on natural gas for power generation, which has made the midstream, gas transmission system one of the most consequential hacking targets in the country. An attack on a natural gas pipeline system could result in parts of the U.S. plunging into darkness for days, since natural gas now supplies 34% of the U.S. electric power. Even more specifically, the North American Electric Reliability Corporation (NERC) states that by 2021, 69% of electricity in Florida will come from gas, followed by 68% in California, 63% in Texas, and 52% in New England.
An attack on the natural gas systems would be detrimental to supplying energy to the United States.
Throughout the entire oil and gas spectrum, facilities are moving, transporting, separating, or reacting hazardous materials through various processes, generally at high temperatures or pressures. The unexpected release of toxic, reactive, or flammable liquids and gases could result in fires or explosions, consequently leading to injuries or deaths. Whether upstream, midstream, or downstream, the involvement of hazardous materials means that there is always the potential for an accidental release, or loss of containment, should the hazards not be properly controlled. Since these hazards can result in injury or deaths, the Occupational Safety and Health Administration (OSHA), which is a sector in the United States Department of Labor, has dictated certain Process Safety Management (PSM) requirements.
A specific PSM requirement that lies on the Operational Technology Network is the Safety Instrumented System (SIS). SIS exists to ensure that should a hazard no longer be controllable, such as a pressure or temperature runaway, level overfill, etc., a process would automatically be forced to shut down. As previously shown, Safety Integrity Systems are now interconnected to Business Networks, 3rd party interfaces, and field instruments. This connection means that a security breach throughout any area of the business enterprise could potentially result in a Process Safety incident. The following list includes examples of cyber intrusions that could result in a Process Safety incident.
Method of Entry - Supplier Interface>SAP> PI>DCS>SIS
In this case, a hacker could enter a Safety System through many layers in the Business Enterprise Network and OT Network from a supplier’s interface. The hacker could raise the set point of an emergency shutdown pressure of a column at a refinery or a gas processing plant to exceed the vessel’s rated design pressure. This change of set point means that when the pressure of the vessel exceeds its design pressure, the vessel could explode, without an automated controlled shutdown. Such an explosion could result in many injuries or deaths.
Method of Entry – Level transmitter>DCS> SIS
Hackers can manipulate a field device to read a certain value. For instance, if they were to force a 0% value in a level transmitter, an operator may believe that a tank is empty and proceed to fill the tank. As the tank level increases, the operator will not see a change and he or she may overfill the tank. An outside operator can stumble upon the overfilling tank in the field and inhale the toxic material, leading to serious respiratory damage. In addition, the materials from the tank may flash and ignite, causing an explosion and/or a fire. As you may recall, a computer “glitch” in Puerto Rico in 2009 led to an explosion, fire, and community evacuation.
Keeping networks secure and safe is critical to ensuring adequate process safety in an oil & gas organization.
As touched on briefly in the Process Safety section, cyberattacks can affect the Health, Safety, Security, and Environment (HSSE) of an oil & gas organization as well.
Method of Entry - Supplier Interface>SAP> PI>DCS>SIS
In the case previously described, in addition to the possible health and safety aspect of employees becoming injured or dying, a company could face severe consequences for violating environmental regulations, as hydrocarbons could be released untreated, directly to the atmosphere.
Method of Entry – Level transmitter>DCS> SIS
In the tank overfill scenario, a land spill could lead to hazardous material run off into community sources of water, rivers, lakes, or oceans. This run off would not only lead to community complaints, but many environmental compliance violations.
Method of Entry - SCADA
As in the case of the 2012 natural gas pipeline hack, attackers could access the control of a pipeline, resulting in the overpressure of liquefied natural gas (LNG) leading to a loss of containment and land spill. This overpressure scenario could lead to the possibility of an explosion and fire, injuring employees and threatening surrounding communities. This event would affect all aspects of an organization’s HSSE Program.
Method of Entry – Oracle EAM>Field Device Maintenance
An attack directly on the Business Enterprise Network could also greatly affect HSSE. For instance, a hacker could target the Preventative Maintenance (PM) schedule in Oracle EAM. Typically, a PM schedule includes safety critical pieces of equipment such as instrumentation associated with SIS or fire and gas detection devices. Environmental compliant regulated equipment, such as analyzers or instruments associated with fired heaters, are also on a PM schedule. If the PM schedule of these devices are changed, not only are the devices likely to fail, but an organization could be violating OSHA’s or the EPA’s compliance standards. In addition to operating out of compliance, people could get hurt and fires or explosions can occur.
Cybersecurity can contribute to keeping people safe and healthy, along with preserving the environment for future generations.
In today’s volatile market, it is even more critical for companies to reduce operational cost, while maximizing production. If a facility is not able to operate at full capacity, it could cost a company millions, if not billions, of dollars a day. This means equipment reliability and production uptime is more critical than ever; however, both subjects could be greatly impacted by a cyberattack.
Method of Entry – SAP EAS>Field Device Maintenance
As previously discussed, hackers could target asset management platforms located on the business enterprise network to manipulate maintenance schedules, such as Oracle EAM or SAP EAS. Such an attack could greatly affect Reliability Centered Maintenance (RCM) programs at operating facilities by disrupting or removing maintenance schedule. For example, if a non-redundant isolation valve, used to control flow on a wellhead during production, is removed from an asset management program, the valve could eventually fail without appropriate maintenance performed on it. If this valve were to fail during a peak production period and production had to halt, a company could lose a significant amount of money each day it takes to repair or replace the valve. The same scenario is held applicable to critical equipment among pipelines and refineries.
Method of Entry- DCS>Field Device
If a hacker were to enter the DCS and manipulate the control of a process directly, the results could be detrimental. For instance, if they were to change the set point of a temperature controller to a value outside of the process design intent, piping could corrode or erode quicker than planned, resulting in an unplanned outage. The outage severity depends on whether or not the system could be isolated; however, there would still be a system out of operation until the piping is repaired or replaced.
Method of Entry- Remote Terminal PLCs
As previously discussed, in 2002 a Venezuelan terminal was hacked through a remote terminal PLC, erasing devices that were critical to oil production. This attack, among other things, led to a reduction in production from 3 million barrels a day to 370,000 barrels a day.
In order to maximize equipment availability and production uptime, networks must be safe and secure across the entire enterprise.
Many countries’ economies depend heavily on the oil & gas industry, which means keeping the market transparent is very crucial to both companies and economies.
Method of Entry – SAP or Oracle
Hydrocarbon accounting and supply chain management is often made possible through SAP or Oracle solutions. By attacking these applications directly, a hacker could modify parameters regarding oil movements and inventories. Business planning, supply, and trading organizations make many decisions based on oil movement and inventory data, which means they will make decisions on false information. If this is the case, the associated market will also respond to the false data.
Method of Entry – Tank Information Management System
A hacker could cause tank inventory levels to read higher or lower than actual by accessing Tank Information Management Systems via the Operational Technology Network. If this were to happen, supply and trading organizations would make decisions based on false data, and the market would respond accordingly.
Method of Entry – PLC, DCS, Field Instrumentation
Hydrocarbon volume measurements greatly depend on a system’s temperature and pressure, which means if these values are inaccurate, so is the hydrocarbon accounting. A hacker could change the temperature or pressure parameter through an instrument directly, a PLC, or the DCS. If these changes occur, the Tank Information Management System will not be able to accurately calculate the inventory of hydrocarbon.
Method of Entry – Automated Tank Gauge (Field Device)
In the case of the 2015 ATG hack, inventories at retail stations were accessible and had the ability to be modified. If this would have happened, traders and analysts would make inaccurate decisions that could affect the market.
Cybersecurity is crucial in upholding a transparent oil market.
A combination of all of the other ideas discussed could result in many financial implications and irrecoverable destruction of a companies’ reputation. If a facility has a fire or explosion, in addition to the financial costs to repair and replace the capital, the company’s reputation and right to operate in a community may be taken away if there are severe injuries or deaths. If there are major safety and environmental violations, a company may be fined and their perceived image may be impacted. The costs of repairing equipment or recovering from an unplanned shut down would greatly increase operating costs.
There are also financial implications for recovering from a cyberattack. Per IBM’s 2016 Cost of Data Breach Study, the total cost of a security breach is $4 million, which is up 29% since 2013.
Cybersecurity involves protecting your financial assets and reputation.
We at Sia Partners work with our clients to help them understand and assess the cyber threat landscape, in addition to determining and implementing mitigations against cyberattacks.
The human element is an important component, if not the weakest link, as it pertains to cybersecurity. It is paramount to engage your staff in the topic of cyber threats and cybersecurity as well as their responsibility of being vigilant within their roles. Sia Partners can help your organization by:
Cyber-attacks Against Oil & Gas Infrastructure to Drive $1.87 Billion in Cybersecurity Spending by 2018. (Jan 29,2013). Retrieved May 22, 2017
2016 Cost of Data Breach Study: Global Analysis from Ponemon Institute. (n.d.) Retrieved May 22, 2017 from
Petrol Malaysia Upstream, Midstream, Downstream. (Sept 2016) Retrieved May 22, 2017
Oil and gas production handbook: An introduction to oil and gas production, transport, refining, and petrochemical industry. (August 2013). Retrieved May 22, 2017
Hackers’ Favorite Target: Big Oil and All That Deadly Equipment (June 10, 2015). Retrieved May 19, 2017.
Global State of Information Security Survey 2016: Oil and gas industry findings: PwC (n.d.) Retrieved May 17,2017
White Paper: Oil and Gas Cyber Security from SAP to ICS Alexander Polyakov and Mathew Geli, ERPScan Retrieved May 17, 2017.
Cyber raises threat against America’s Energy Backbone (May 23, 2017). Retrieved May 23, 2017
Oil and Gas Cyber Security – Questions and Answers (December 23, 2015). Retrieved May 17, 2017
TWA Article- Internet of Things in the Oil and Gas Industry (February 23, 2017). Retrieved May 22, 2017
Safety and Health Topics: Process Safety Management- United States Department of Labor. Retrieved June 1, 2017