Carbon Accounting Management Platform Benchmark…

What are the best practices to build the DevSecOps framework that drives a secure software development lifecycle and allows organizations to improve team collaboration, time-to-market, and improved productivity?
Understanding and addressing the cybersecurity risks posed by external or internal actors has never been more important than now as IT departments in modern organizations have more customer-facing applications and websites. The risks are further compounded by a growing number of attacks during the Covid-19 pandemic due to the increase in the number of attack vectors hackers can target (e.g. - remote workers were attacked in hacks involving data theft and malware). As organizations have widely implemented the DevOps (Development + IT Operations) model, they identified existing gaps in its security. DevOps is a set of software development tools and processes that combine software development (Dev) and information-technology operations (Ops) to shorten the systems development life cycle, overlooking the security checks during the application development. Security checks for most applications are not even conducted. If they are, they only take place on major builds/ releases. For the instances where the security checks did take place, they were conducted toward the end of the development cycle which gave hackers room to insert malware into an application during the build process. These types of Security checks act as a brake pedal and slow down the deployment process in order to ensure all checks are complete before the Go-Live, which could take weeks in certain cases. Security was always an afterthought and less prioritized than development which resulted in a reworking of code or applying security patches post-release.
Due to the growing number of cybersecurity attacks where hackers leverage application vulnerabilities in the source code or in the framework the application is built upon, it is important and urgent for organizations to secure their applications using a set of robust principles and frameworks.
DevSecOps (Development + Security + IT Operations) is an augmentation of DevOps (Development + IT Operations) to allow for security practices to be integrated into the DevOps approach. The traditional centralized security team model must adopt a federated model allowing each delivery team the ability to factor in the correct security controls into their DevOps practices.
A federated model allows for better collaboration between the development and security teams. In a federated model, though the policies and guidelines are established under the CISO, the security and development teams for each application have ownership over how they are to be implemented as every application and business line is different.
DevSecOps is a concerted effort in shifting security left in the Secure-Software Development Lifecycle (SDLC) by requiring a cultural change in organizations to encourage “Security as Code” with collaboration between engineers and the security team. DevSecOps enables firms to secure their applications starting from the build process, and without DevSecOps practice malware might not be discovered until the application is distributed to thousands of customers. It also allows organizations to keep up with the rapid pace of development in the DevOps model, to deploy applications securely and at scale.
The DevOps and DevSecOps processes consist of six main high-level stages, however, the focus in this paper will be on the three stages of Build, Test, and Deploy where DevOps and DevSecOps differ:

DevOps Pipeline
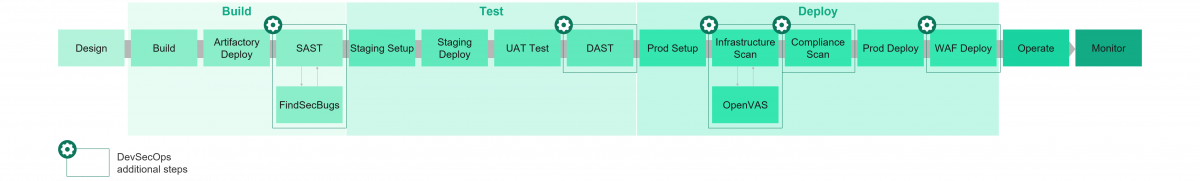
DevSecOps Pipeline
Though the high-level stages are the same in DevOps and DevSecOps, the differences arise in the specific steps in each stage. As the pipeline diagrams depict, DevSecOps involves integrating static scanning (SAST) of source code in the build stage, Dynamic application scanning (DAST) in the test stage, and finally Infrastructure & Compliance scan and a Web Application Firewall (WAF) in the Deploy stage.
Once an organization’s leadership and their teams understand the benefits of moving from a DevOps to a DevSecOps model, it is important to adapt the necessary processes, tools, and technologies to ensure the culture and execution are on the same page.
Below are some recommended ways for an organization to get started:
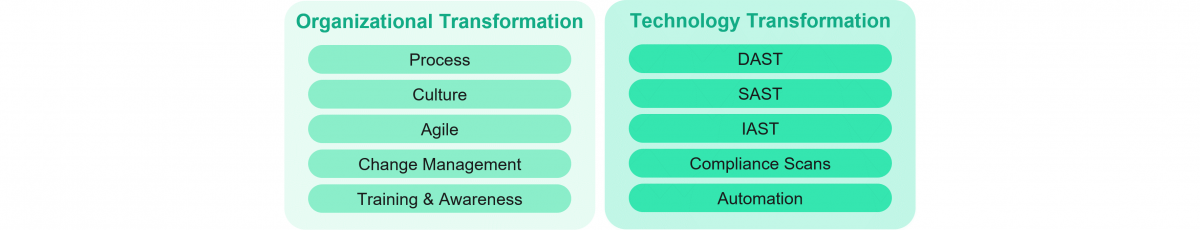
Automation can and should be leveraged in DevSecOps to take it to the next level of maturity. The scanning tools mentioned above can be used to manually scan applications or they can be automated. Organizations that have automated all or most of the scans greatly benefit by reducing time to market for the application and having a standardized process.
DevSecOps main benefit is to improve the security posture of the organization which also results in instilling confidence in the customers and increasing your credibility.
By shifting left in the SDLC process, organizations can identify and fix security vulnerabilities much earlier in the life cycle resulting in lower costs to fix them and instilling a culture of security and collaboration in your entire organization. Organizations save anywhere from 2 weeks to 6 months in development efforts to address the code vulnerabilities using a DevSecOps approach instead of the traditional DevOps approach with app scans at the end of the deployment phase or a waterfall development method. DevSecOps is also extremely important for organizations to comply with industry standards and best practices such as National Institute of Standards and Technology (NIST), Application Security and Development (ASD) etc. Specific NIST guidelines to information security testing and assessment.
In summary, with the right people, processes, culture and technology in place, businesses will have a better understanding of how to handle security for their applications. This can reduce the likelihood of a cybersecurity breach caused via exploiting the applications. Along with a strong DevSecOps program in place it is also recommended that organizations still conduct source code reviews periodically to catch for unknown patterns in code that could potentially be exploited but aren’t caught by tools in the DevSecOps process.
Implementing effective DevSecOps measures can be challenging. One of the major challenges’ firms will have to face is dealing with the cultural change that comes with shifting from a DevOps to a DevSecOps approach. Below are a few key questions management teams should consider while evaluating the robustness of their DevSecOps program or shifting to one if it does not exist:
In consideration of these enhanced cybersecurity challenges posed by third-party vendors and magnified by remote working and virtual communication, Sia Partners is ready to assist our clients with implementing DevSecOps and best practices to keep firms up to date with the latest innovations.
Assisting Clients Transition from DevOps to DevSecOps:
Assisting Clients with Vendor Selection:
Governance, Risk & Regulatory Compliance:
Automation:
Performing Scans for Clients: