Carbon Accounting Management Platform Benchmark…

Each year, SWIFT releases a new version of the security controls applicable to network users. This year, Sia Partners is highlighting the changes in the CSCF and why they're important.
The Society for Worldwide Interbank Financial Telecommunication (SWIFT) network connects more than 11,000 financial institutions across over 200 countries. Every day, millions of payment orders, purchase orders, transactions and more, are executed via the SWIFT network. It acts as a true catalyst, accelerating the speed of financial transactions worldwide. However, it is increasingly threatened by a rising number of cyberattacks and financial frauds.
In response to a cyberattack on the Central Bank of Bangladesh, which resulted in the theft of $81 million, SWIFT launched the Customer Security Program (CSP) in 2016. This security strategy is based on the Customer Security Controls Framework (CSCF), which sets out requirements for securing financial transactions.
Since its launch in 2017, the Customer Security Controls Framework (CSCF) aims to strengthen the security of the SWIFT community by maintaining appropriate cybersecurity hygiene, thereby reducing the risk of cyberattacks and minimizing the impact of fraudulent transactions. It relies on three primary objectives designed to prevent, detect, and respond to cyberattacks. These three objectives are supported by seven security principles, carefully defined with industry experts.
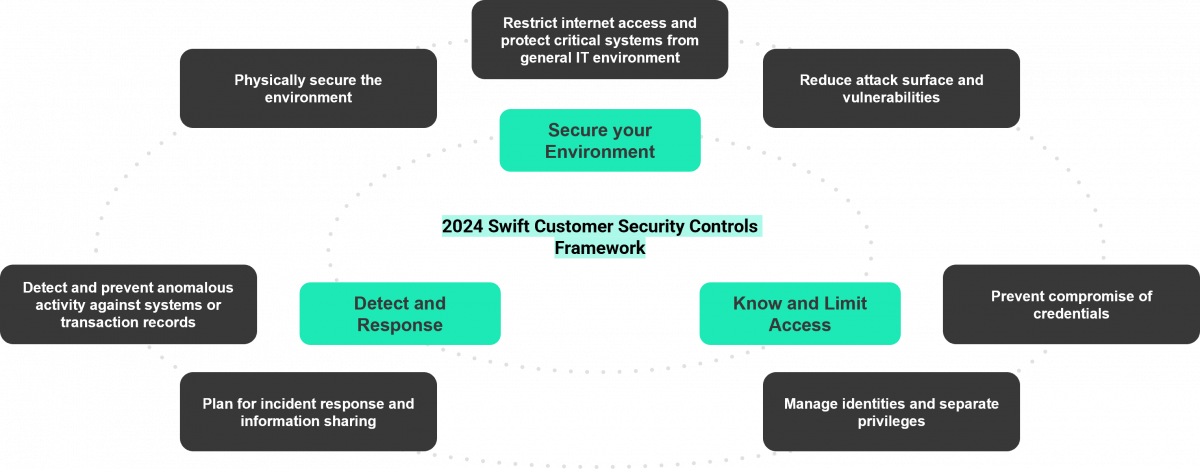
These security principles are embodied by 32 controls, of which 25 are mandatory. The deployment architectures of SWIFT services affect the scope and applicable control measures for each institution. There are five types of architectures deployed within member organizations: A1, A2, A3, A4, and B. These architectures are distinguished by specific characteristics within the information system:
Architecture A1: The user possesses both the communication interface and messaging interface.
Architecture A2: The user only possesses the messaging interface, but not the communication interface.
Architecture A3: A SWIFT connector is used in the user's environment to access an interface at a service provider or with SWIFT services.
Architecture A4: The user uses a server to establish an external connection with an interface, application, or solution related to SWIFT at a service provider.
Architecture B: No specific SWIFT component is used in the user's environment. Access to SWIFT services is carried out via an application or back-office system of a service provider.
Since Russia's invasion of Ukraine, and the subsequent exclusion of Russian banks from the SWIFT network in 2022, the number of cyberattacks against the Belgian company has continued to increase. SWIFT is a prime target for Russian cybercrime. Indeed, were the SWIFT system to be unavailable for several hours or days, this would be devastating for the Western and global economy. However, this is hardly imaginable as it would require a coordinated physical and/or cyber-attack on the three data centers located in the Netherlands, Switzerland, and the United States. Additionally, SWIFT takes the security of its system very seriously and has a robust control environment for the security of its digital and physical infrastructures.
The new version of the SWIFT CSCF includes several modifications and clarifications. Below is a summary of the major changes:
To address the increasing use of the Cloud and the outsourcing of information systems, Control 2.8 "Outsourced Critical Activity Protection" has become mandatory.
To support the deployment of Control 2.4 "Back Office Data Flow Security," certain changes have been made regarding the securing of servers, data exchange security mechanisms, and network segmentation.
Recommendations related to USB port protection are now included in Control 2.3 "System Hardening."
Control 2.9 "Transaction Business Controls" now specifies that transaction controls can be performed outside the secure zone.
Control 7.4 "Scenario-based Risk Assessment" now states that existing risk management processes can be relied upon.
To obtain a compliance certification, it is necessary to comply with the mandatory controls defined for your architecture type and, by the end of the year, undergo an independent assessment of your IT system as a SWIFT network user. This ensures that the controls examined meet the control objective, cover the relevant components, and address risk factors.
SWIFT has designated Sia Partners as a cybersecurity service provider following a thorough review of our strategic orientation, experience, cybersecurity credentials, reputation, and commitment to our clients in the financial sector. This trust is a recognition of our experts' extensive knowledge of the CSCF and cybersecurity in general. Indeed, with a proven methodology for audit and compliance, our experts can assist you in implementing all the controls resulting from the CSCF.